Back in early November I was given a small investigative task. A public person had been approached in a strange fashion and they felt it was an attack on their reputation brewing. After examining the particulars of the situation, I had several other possible interpretations that seemed more likely. The best fit is that a cybercrime group has spoofed Status Labs, starting no later than July of 2022, and their motivation is extortion. I only have one victim data point and the company has demonstrated a focused disinterest in even hearing about this. I have no estimate of when the active exploitation attempts began, who the set of potential victims are, nor how far the perps have gotten in their schemes.
For those just arriving, this is practically an instant replay of yesterday’s Sovereign Challenge Unmet. This post contains the trail of how I went about attempting to contact Status Labs, and closes with some thought on how such problems SHOULD be handled.
Attention Conservation Notice:
Some pretty techie domain/email stuff in here, but it’s a master class in how to NOT protect your brand when a cybercrime group has assumed potions of your firm’s identity. This is a followup to the anonymized Actual Incident Response Today.
Genesis:
Status Labs, who use statuslabs.com as their official presence, failed to secure statuslabs[.]co, and they don’t appear to be checking their logs for weird HTTP redirects. The setup of the spoof began no later than July 12th of 2022. RiskIQ is not perfect; the “Expired 5 months ago” seen here is an artifact, I checked the spoof domain right before I started writing this on Thursday and it’s still active. The bad guys aren’t sleeping either - three weeks ago that site responded to requests over Tor, today it most pointedly does not, and Friday morning I had a different indication that they’re actively monitoring it.
Hosting Particulars:
Here’s the actual Status Labs domain. That’s the results of a Maltego L1 footprint machine, then I cut it down to just the important stuff and made it a single page.
Here is the statuslabs[.]co setup. There’s an external service they’re using to post articles about the target, that’s the obscured stuff to the left. They’ve spoofed at least one employee, acquiring an Austin area phone number to match the company HQ location.
Doppleganger:
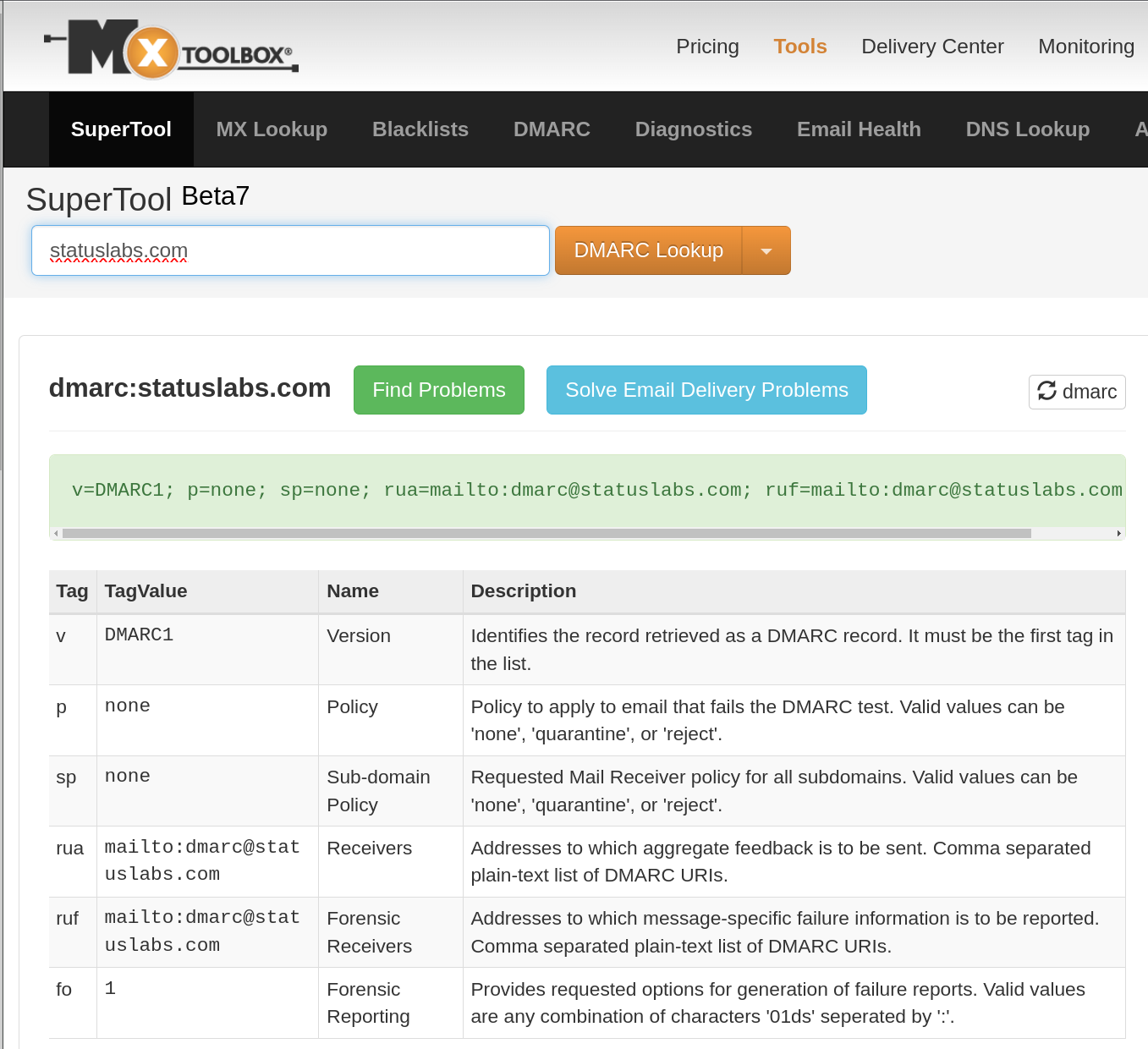
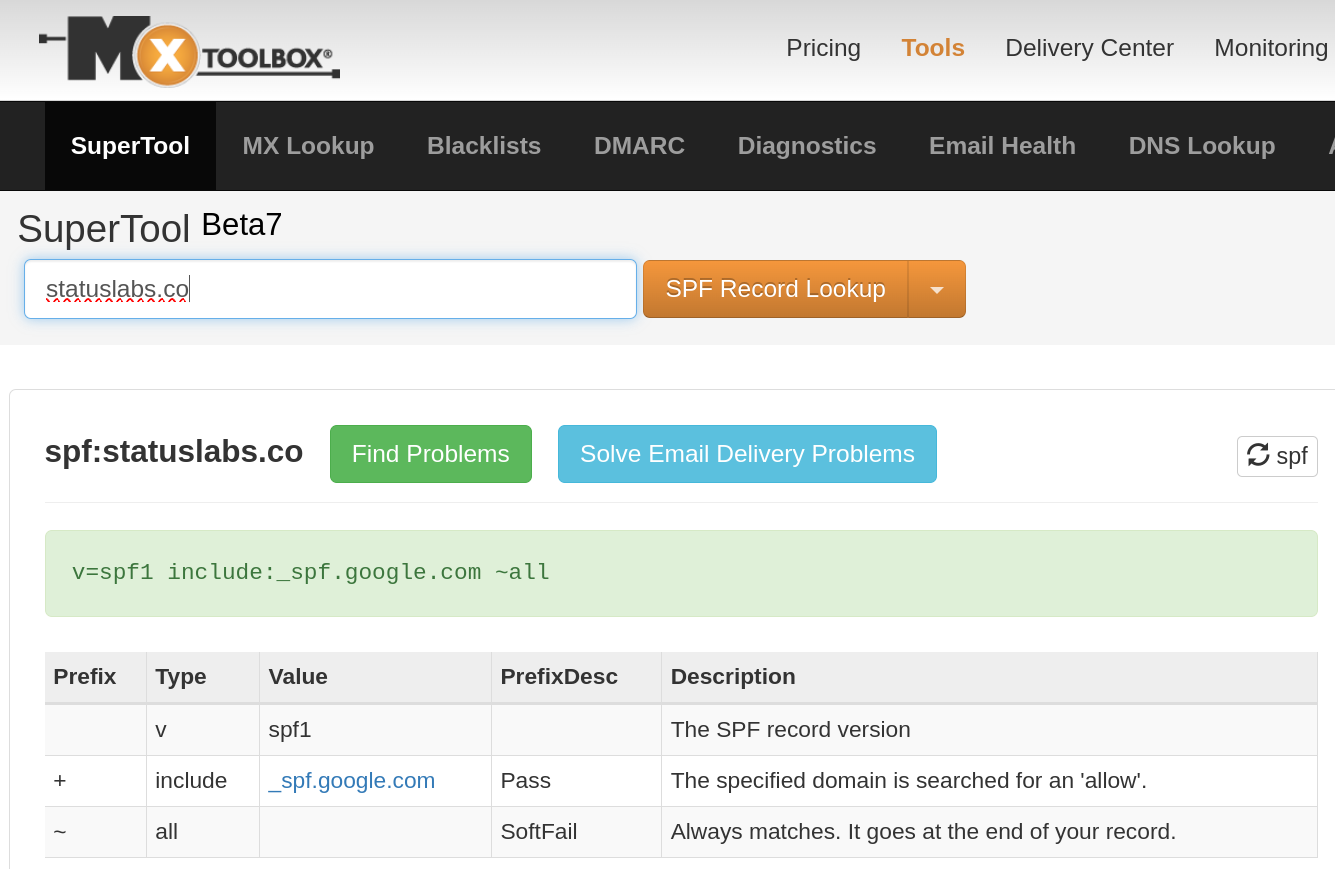
Here’s the core of the problem. Status Labs uses Google Workspace, they’ve got a permissive DNS/email configuration because they run a mailing list, and this left them open to being spoofed.
Here’s the details of the mail configuration, first the legit statuslabs.com stuff. Note the lack of DKIM message signing.
And here’s the cloning effort.
Responsible Disclosure:
Here’s a public LinkedIn thread that anyone from Status Labs could have viewed to get a sense of the problem, without tipping anyone off regarding the name of the company or the target. The “fiat justitia ruat caelum” is where I decided I had met the good Samaritan requirements for private disclosure.
I tried contacting the principals and a few other high level people at Status Labs. I am sure more than one of them read the LinkedIn post.
And I finally made contact with an actual person tangentially connected to the organization, which I mentioned in my outreach to Status Labs chief of staff Clair Rogers.
Here’s the one chance they had to handle this issue quickly and quietly.
Here’s a transcript of the two minute voice message I left for them
Those guys are one of their domain is being spoofed and someone has cloned one of their employees. They are approaching high net worth, high visibility individuals and it looks like, extortion type stuff happening. This absolutely … it's got to be done by calls. I can't tell for sure if the bad guys are inside their infrastructure. If they are and they start having email cascades about what's going on and if it's one person that's been compromised, that's the kind of thing that would set off ransomware for the org or all of their data and all their clients have been extracted and it's suddenly available on the dark net. I mean, they're just, it's an absolute nightmare scenario. What I have to go do will take an hour to an hour and a half and then I will be available, probably clear up until midnight Pacific time. If they want to talk tomorrow, like I said, I'm on a super irregular schedule. I just need a little advanced notice and basically about a 10 minute call with whoever is responsible for their security stuff. I would be able to convey the particulars of what's happening and hopefully I'm just being a little bit to jumpy about stuff and this is something that's purely outside the organization and they will be able to quickly and easily shut it down. So cross your fingers and talk to you soon.
Giving Up:
The person who responded by Signal then ghosted me. And having read this stuff in the Status Labs Wikipedia entry, I decided a public piñata party was an entirely appropriate next step.
In 2015, Status Labs co-founder Jordan French resigned as chief executive officer after fallout and public outcry stemming from the February 2015 demolition of Jumpolin, a piñata shop in Austin.[11][12][13] In October 2014, Status Labs co-founders French and Fisher bought the land on which the Jumpolin shop stood through their F&F Real Estate Ventures.[14][15][16] The partners commissioned a demolition crew to demolish the store in their attempt to clear the lot for a SXSW-timed stage event.[15][16] The tenants said French and Fisher gave them no notice of the demolition, that their inventory was still inside the building, and that they had more than two years left on their lease.[17]
Assessment:
So what COULD be happening here?
Company spoofed by extortion artists seeking financial gain.
Company spoofed by corp or foreign intel seeking to run campaigns against high visibility individuals.
Disgruntled former employee OR a well heeled client has a grudge and this is payback.
Status Labs competitor is doing this for some reason, but I can’t fathom how they would benefit from it.
Employee at the company is a poor performer, but has some technical skills in their network, and decided this was a good lead generation strategy.
Company itself is actually behind the statuslabs[.]co and are doing these things as a bottom feeder lead generation strategy, but with plausible denial built in.
I ranked those six theories in what I thought to be the order of likelihood. Here’s what makes me think grifters:
If this were a corporate or foreign intel effort there are MANY things they could have done to further obfuscate the spoof. As an example, they could have got a Cloudflare account of their own, 100% cloned the actual Status Labs domain’s visible stuff, and I would have had a MUCH harder time untangling things.
I’m not sharing the details of the approach, but I think a competitor or former employee would have done things in a very different fashion than what the victim actually received. Keep in mind I have significant advocacy and elections experience in the U.S. and Europe.
The company itself seems to be a leader in their field. It would be even worse judgment than the process that led to the piñata store demolition if they are directly involved in some fashion.
Worst Case:
When I received the tasking for this, I spent quite a bit of time looking at it. Then I slept on it. Then I spent more time looking. Once I developed an opinion on what was happening, I attempted to contact the company, INSISTING on voice calls. Here are the reasons I did that:
Looks like just an extortion operation, but those things are always part of a larger network, and if the original players became concerned they were going to lose their foothold, they could potentially broker their access to a MUCH more dangerous predator.
Doesn’t look like the perps have administrative control of the official Status Labs domain, but it’s entirely possible they spearphished the employee they’re spoofing, and that they have some visibility to internal communications. That would make sense in light of how long they’ve remained undetected - as if they’re intercepting any email contacts to that person and eliminating the ones that would exposre them. If the company foolishly sends an all hands email about the problem, that turns the theoretical sale of the foothold from potential to an immediate business need for the grifters.
That theoretical more dangerous predator might already be in position for the day the hand to hand grifts stop working. They could have already extracted all the client data from Status Labs. They could ransomware the company, collect the payment, stiff them on the decryption keys, and instead auction their customer base to the highest bidder.
Instead what I think happened is that they Googled me, saw the results of a smear campaign that’s been aimed my way since 2010, and they jumped to a conclusion based solely on their expertise in just one problem domain. That’s similar to what the intended victim did in terms of their reputation, but they had the good sense to quietly consult others, and one of those others knew that it was time to summon me …
Attribution:
So what do we have on the individual(s) operating the statuslabs[.]co domain?
Someone paid for that domain and various web enabled vendor sites were accessed, which will have a trail of credit card data and IP addresses.
Google Workspace account scott@statuslabs[.]co is in use, there’s a search engine finding of john@statuslabs[.]co, and neither of those are the name of the employee being spoofed. Again, there will be credit card data and IP addresses, as well as who they were targeting.
The spoofed employee offered a mobile phone number with the area code and exchange of a mobile carrier in Austin. A pretext call to it revealed a voicemail with a generic sounding female attendant voice.
The spoofed employee’s email must be monitored. Prior work I have done involved interpreting responses to both subpoenas and search warrants. If the operator of the account is using a cell phone there will be GPS location data available as well.
There is another service connected to statuslabs[.]co which can be seen using RiskIQ. This appears to have been used in other campaigns besides the one against Status Labs.
It’s really a shame this wasn’t quietly escalated to the Austin FBI field office. Now that it’s public the element of surprise is lost. The points I made are still valid but the potential to elicit further information is gone.
Conclusion:
Based on the role of the person who first responded, but then ghosted me, it’s reasonable to assume that at least one of Darius Fisher, Jesse Boskoff, or Claire Rogers was part of the decision to ignore this problem. The cybercrime reporter who has seen the investigation details has said it’s not a story until there’s a second verifiable target. If someone else contacts me I will make that introduction.
Had I seen an aggressive, professional incident response, including the aforementioned escalation to the FBI, there’s a very good chance I would have quietly stepped back, and the intended target would be happily assisting in cornering the perps. Now that my name is publicly associated, not only is that opportunity is gone, this situation will quickly come to the attention of others, and that will likely add a great deal of noise to the signal.
Given the nature of Status Labs’ business, the size of the company, and the level of hazard this represents I am sure corporate counsel will be involved in the belated incident response. Everything I referenced in writing this post is based on readily available public information and it only became visible after Status Labs ignored a focused, well documented effort to contact them privately. It would be instructive to read Rauhauser v. McGibney, my precedent setting 1st Amendment case related to the Texas Citizens Participation Act, and wise to carefully review my OIG complaint against the Dallas FBI field office. I do NOT suffer fools gladly.
Like SOCOM and what I described in Sovereign Challenge Unmet, Status Labs has a real problem here, and it started with a lack of situational awareness regarding their brand. Despite the nature of their business, they also lack any discernible cybersecurity contact, which I find mildly astonishing, here at the end of 2023. Given the way the world is headed I think we all need to examine our attack surfaces, because these two stories are in no way unique.