Roger Stone has been involved in Republican election trickery since the Nixon administration, famously sporting a tattoo of President Nixon between his shoulder blades. Stone was responsible for the Brooks Brothers riot in Florida during the 2000 election, his associate Jerome Corsi was the mastermind of the 2004 Swiftboating of John Kerry, and he was sentenced to three years in prison for obstruction of justice, false statements, and witness tampering during the Congressional investigation of Russian interference in the 2016 election. Trump commuted Stone’s sentence and he never served so much as a single day.
While Stone is in the news again, having been caught on tape discussing an assassination plot, there is an older, esoteric trail of clues regarding his social botnet, which has never been fully investigated.
Mueller Investigation:
The Mueller investigation involved an appearance by Stone’s social media advisor, Jason Sullivan, in June of 2018, but they went no deeper than interviewing just him. The botnet’s access to the Twitter API was suspended in September of 2019 and then it finally received some attention from Business Insider in March of 2020 due to its involvement in promoting Qanon conspiracy theories.
I first noticed the Power10 botnet thanks to work by Jess Hernandez and Twitter personality @conspirator0, adding it to my ongoing recording of the information operation that led to the January 6th attack. The entire collection of 220 million tweets and user profiles began in July of 2019 with the White House Media Summit, and the whole data set was made available on Figshare in Twitter’s academically citable “dehydrated” format on April 2nd of 2021.
The nature of what this application did on Twitter was fairly pedestrian, it was just a group amplification app. It was notable for who was using it, what they were boosting, and that the Power10 app survived the great bot pogrom of 2018, which happened after Twitter completed their acquisition of Smyte in June of that year. Some seventy million accounts and 143,000 applications were removed that summer, creating a notable noise reduction signature in large datasets.
January 6th Committee:
The January 6th Committee issued subpoenas to the following social media companies. The four in bold were overtly partisan in nature and their executives were at a minimum aware of what was happening.
4chan
8chan/8kun
Facebook
Gab
Google
Parler
Reddit
Snapchat
Telegram
TheDonald[.]win
TikTok
Twitch
Twitter
YouTube
Zello
Both Gab and Parler were subject to leaks that made it to DDoSecrets. TheDonald.win was also available but it is unclear if the whole content remains accessible at this time. The 8chan leaks did not make it, but that data was broadly available. The availability of the Parler data fueled the FBI’s January 6th investigation thanks to the Sedition Hunters.
The data related to the Power10 app was made available via Figshare, but in what Twitter calls “dehydrated” format. Only the numeric IDs of user profiles and tweets are allowed, and anyone seeking the full data must “rehydrate” the content using the Twitter API. The API is no longer freely available and much of what mattered was deleted when the accounts involved were suspended.
My internal system, based on ArangoDB and Elasticsearch, contains a “hydrated” cache of a quarter billion Twitter account profiles about about a billion tweets. This is useful for research in the area, but as it’s no longer possible to reproduce the content directly from the Twitter API, it is at best intelligence, rather than evidence.
Twitter Activity:
There were thirty one notable accounts using the Power10 app.
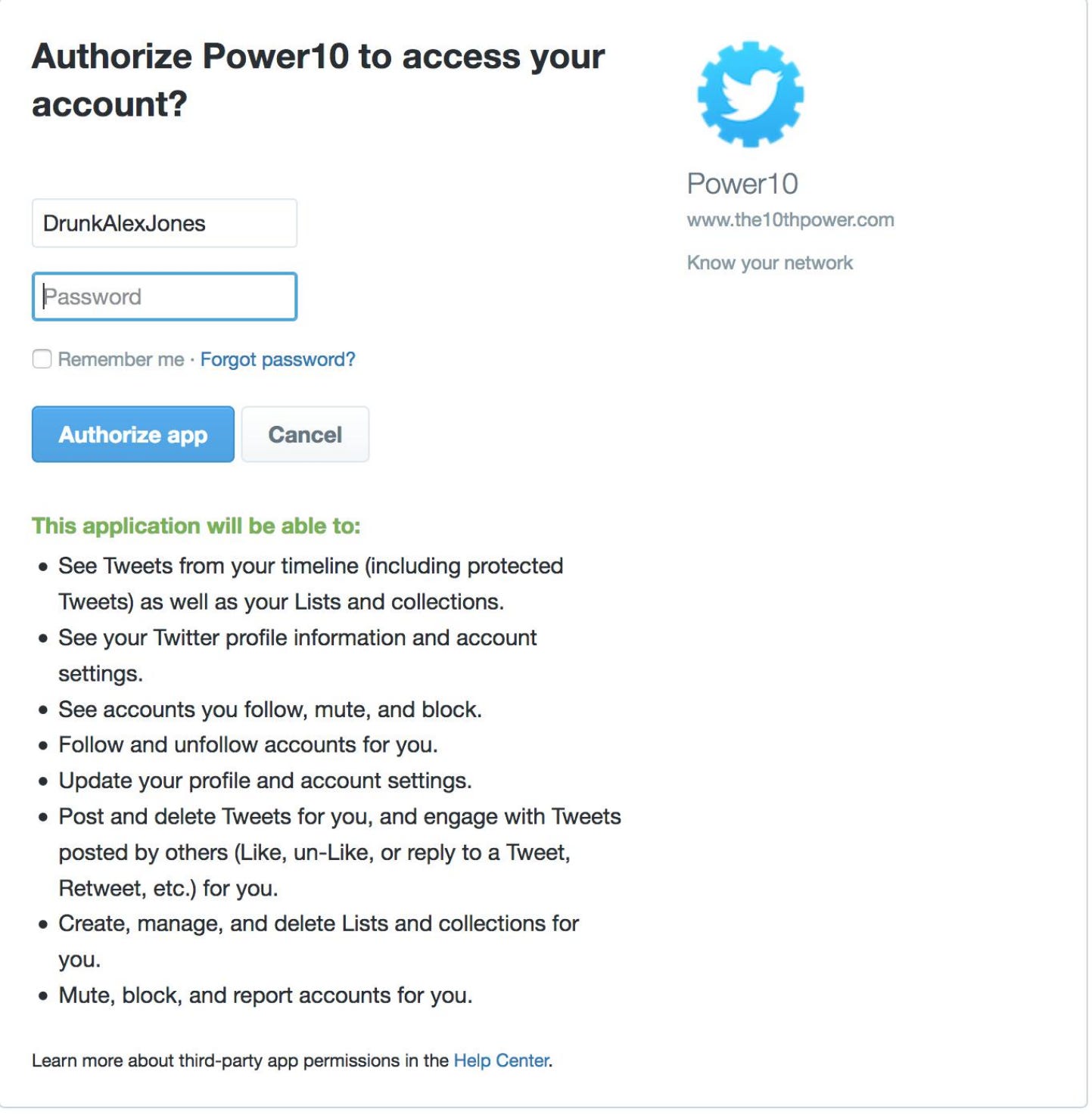
@conspirator0 captured this screen shot while signing up for the service with his @DrunkAlexJones experimental account. Note the domain name used.
Hosting Mysteries:
The reason I keep coming back to this application is not so much how it was used on Twitter, it’s the intriguing entanglements it has in terms of its creation, development, and hosting. My work in this area involves the Maltego cyber investigation platform, a RiskIQ researcher’s account, BuiltWith’s web site technology profiling service, and Maltego’s access to the Internet Archive. This work is reproducible, but it requires the €1100/year Maltego license and substantial access to a DNS intelligence service such as Farsight or RiskIQ.
Any domain referenced in this article will be “defanged” by placing square brackets around the final period in the name. This is an infosec convention that allows the sharing of potentially hostile sites without triggering an accidental visit, as shown here.
example[.]com
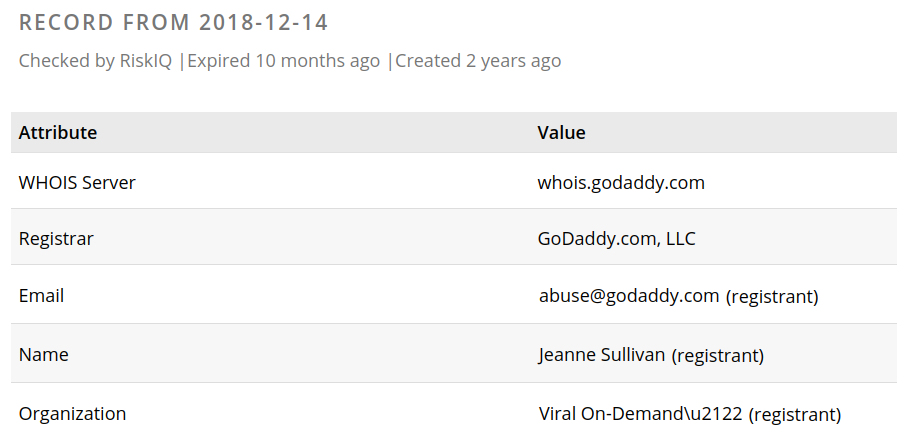
The domain used, the10thpower[.]com, was registered by Jeanne Sullivan, Jason’s mother, using the email jeannesullivan3@gmail.com. Someone has gone to the effort of scrubbing this data from RiskIQ, but there are screen shots of it, and this shows one of Jason Sullivan’s companies, Viral On-Demand.
Jason Sullivan is known to use guardianlion@gmail.com for domain registrations, one of them is thetenthpower[.]us, and this has not been scrubbed. If criminal activity were to be discovered in connection with the Power10 app, that scrubbing might qualify for an obstruction of justice charge.
We processed Roger Stone's internet presence using RiskIQ. He appears to have employed a Canadian individual named Andrew Dion during 2016, who shortly thereafter showed he was working for Datablocks, a Canadian firm which was fined $100,000 in 2018 for installing malware via online ads.
Whois data for Stone’s Vote Protectors domain shows it was proxy registered around August 4th of 2016 and left to expire a year later. The system was hidden by the Cloudflare CDN for the first six months, after which Cloudflare protection lapsed, revealing the domain was being hosted with GoDaddy.
We first noticed the name Vote Protectors while reviewing domains that are clearly attributable to Stone. Stone openly promoted Stop The Steal, and Vote Protectors appears just once, in the cookies page. The phrase “Vote Protectors” is used in some of the Stop The Steal literature.
Stop The Steal was sued and Vote Protectors looks like it might have been a stealthier replacement. Examining Stop The Steal resolutions during this time we see signs of IP addresses from Amazon and Tiggee, LLC hosting. One was cited in VirusTotal, but there was no associated hash, or fingerprint of malware. This bears further investigation from those with technical expertise in the area. Vote Protectors resolutions shows no signs of such a slip.
On October 27th the Vote Protectors site redirected via an HTTP 301 message to Stop The Steal . If you scroll to the bottom of the August 14th capture of the site you will find the following three pieces of information:
andydion@a2plcpnl0494.prod.iad2.secureserver.net
15194047625
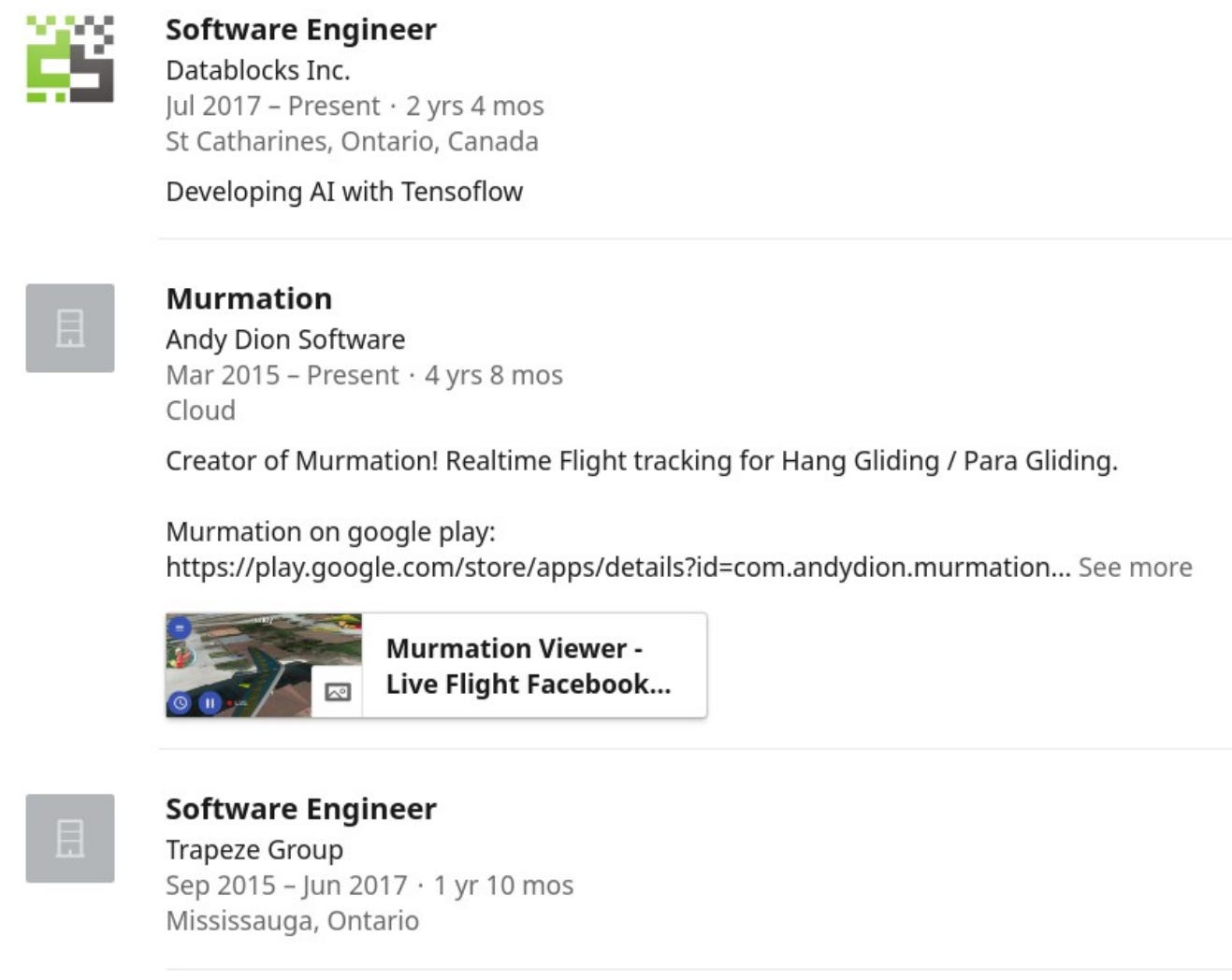
Andy Dion is a first and last name. The hostname after the @ sign resolves to 198.71.235.90, a mail server within GoDaddy. The last is a North American phone number, 519-404-7625, in the vicinity of Kitchener, Ontario. A little bit of Google use yields a LinkedIn profile for Andy Dion in St. Catharines, Ontario. Dion's work history appears on the following page. He was at Trapeze Group during the 2016 U.S. Election, then shifted to Datablocks in July of 2017. He lists ongoing private work of his own spanning employment at both companies.
This is what can be plainly observed with the Wayback Machine and RiskIQ. It seems more than probable cause to dig further into what sort of work Dion did for Stone.
Enter Alex Vidal:
Sullivan and Stone came to a parting of ways, as reported by The Daily Beast in God Declares Swamp Drained at Mar-a-Lago Super PAC Fundraiser.
On his website, he proudly boasts that he was “hired as Chief Social Media Strategist to Roger J. Stone Jr.” Asked about Sullivan’s new super PAC, Stone told PAY DIRT, “if Jason Sullivan is involved, it’s probably a scam.”
The @AlexJVidal Twitter account has been through some things the last five years, but this image used to be the pinned tweet for the account.
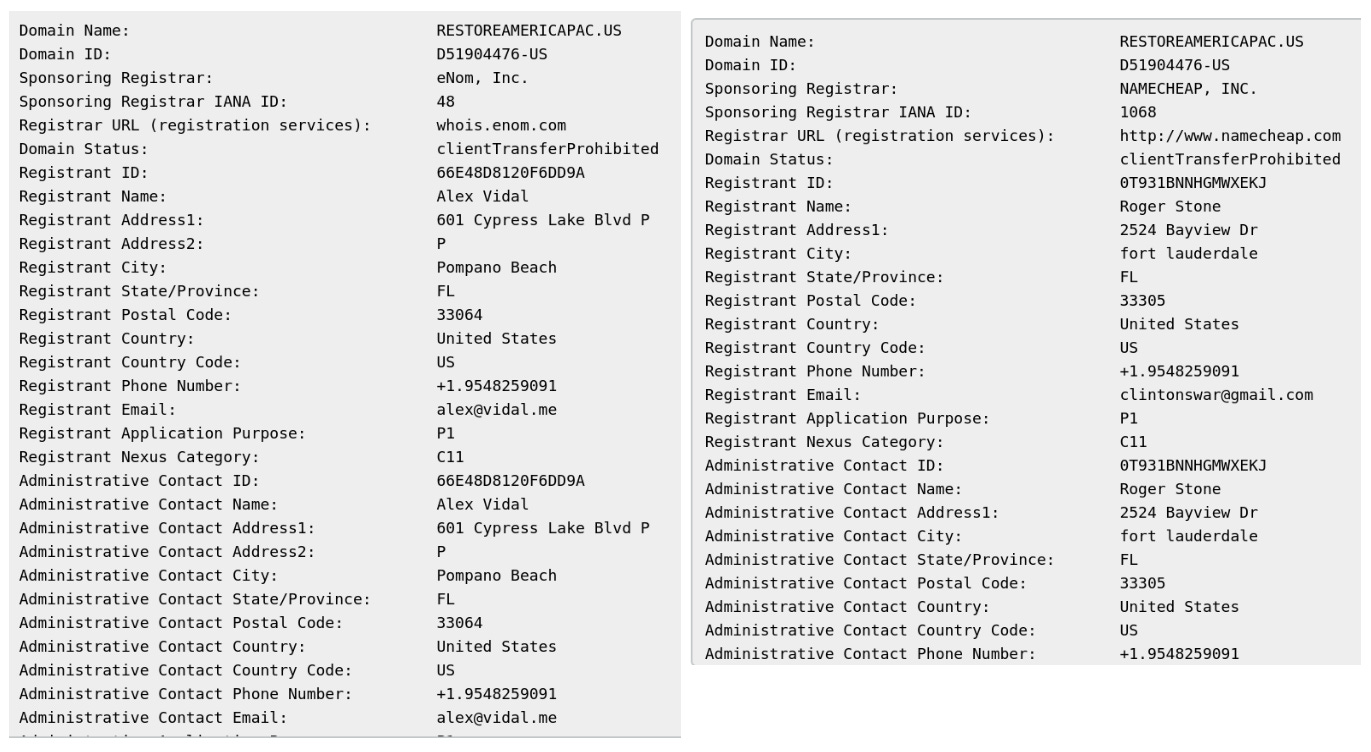
Vidal is involved in the administration of domains owned by Stone. Here is a domain registered by Vidal, then later passed to Stone, but still using Vidal’s cell phone.
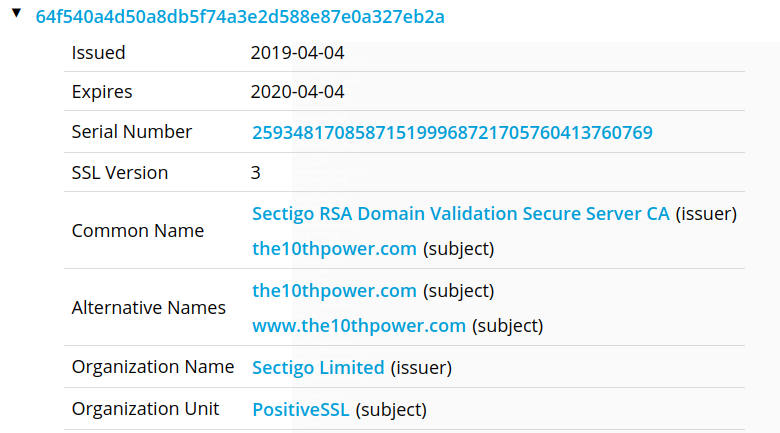
Here is something less direct, but it's important. The domain for the amplification app Power10 was switched to Sectigo as an SSL certificate provider in April of 2019.
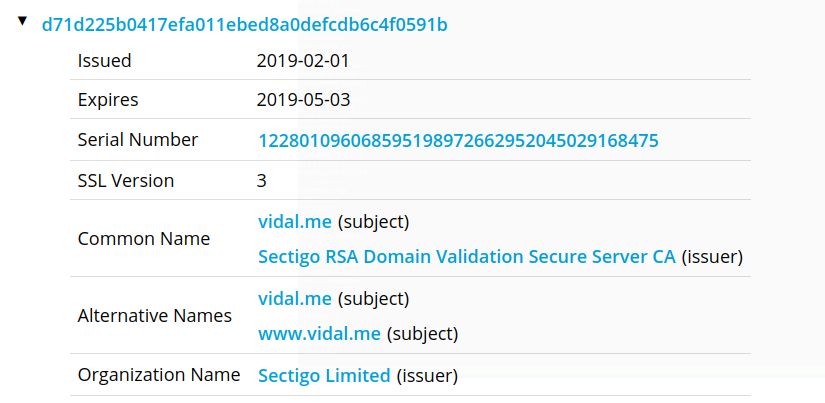
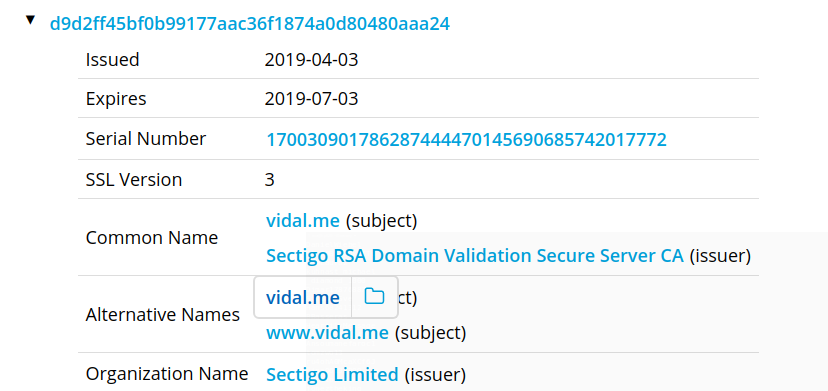
The rest of Sullivan's SSL certs are Comodo, GoDaddy, etc. This is the only one from Sectigo. But Vidal began experimenting with Sectigo two months before The10thPower moved.
And his personal domain changed Sectigo certs again within the same 24 hour window as The10thPower.
Alone, the correlation of SSL providers wouldn’t be such a big thing. When taken in context with the rest of it, someone paid for the Sectigo certs, and that would have been within easy reach for the FBI, had they pursued this in a timely fashion.
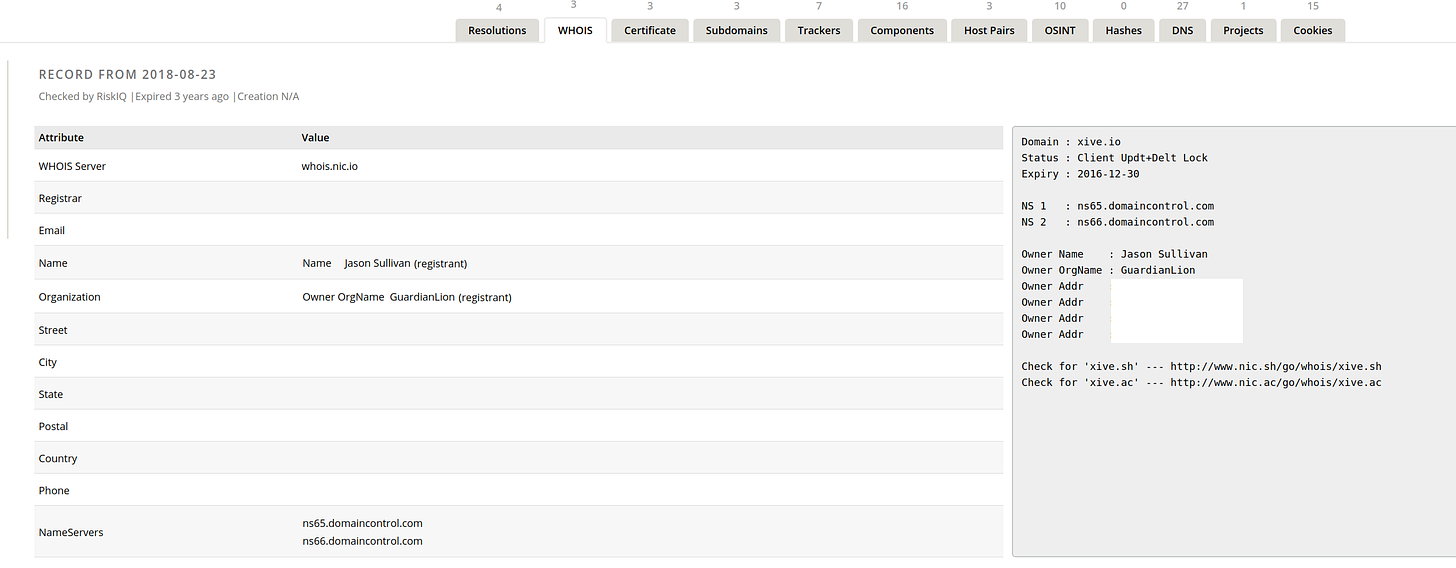
A Missing Mystery:
Today RiskIQ does not show any sign that Jason Sullivan once owned xive[.]io, everything on the domain stops in September of 2018, but five years ago you would have seen this.
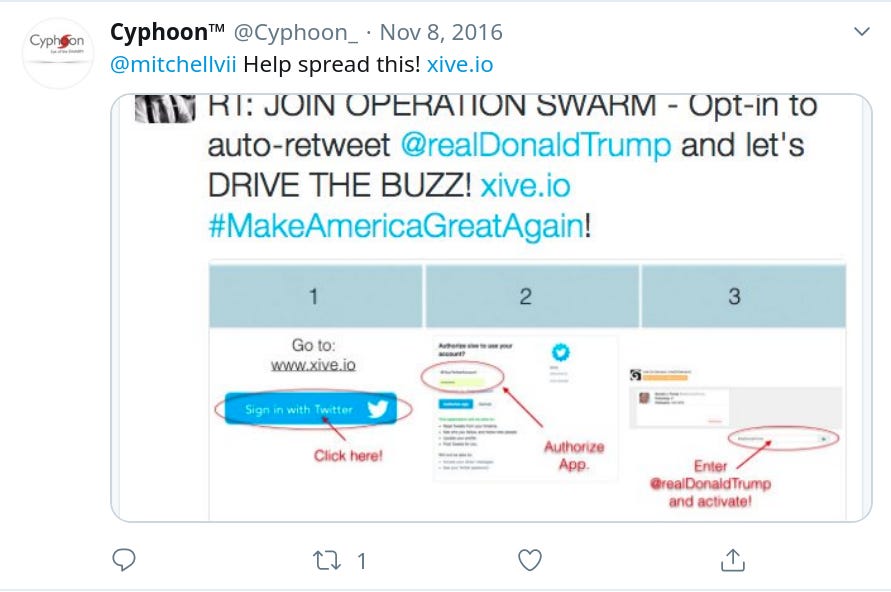
And this is what xive[.]io is really interesting. Here’s Cyphoon, Jason Sullivan’s company, boosting a tweet from Roger Stone that shows xive[.]io to be the home of OPERATION SWARM.
Examining xive[.]io using The Wayback Machine is fruitless; the first capture was November 23rd of 2018. If I had not kept these screen shots there isn’t any way to reconstruct any of this.
And this trail going missing is extraordinarily convenient, no?
The Disinfodrome Document Cache:
I run a system called Disinfodrome, which is an instance of Open Semantic Search populated with all the documents from these investigations.
Active Measures 2016 U.S. Senate
Crossfire Hurricane
Congress January 6th
Mueller FD-302s
Mueller Report
January 6th Transcripts
January 6th Final Report
There is no mention at all of Power10 or any permutation of the name. There are no appearances of the name Vidal. The name Dion appears just five times, but it’s always Dion Cini, a witness interviewed by the January 6th Committee.
Assange & Stone:
I am not sure precisely what happened but there is a great deal of energy in the hacker realm right now. People are digging through files from the 2010 - 2012 time frame, frantically throwing spaghetti at the wall. I am told this has to do with Julian Assange’s Second Superseding Indictment of June 24th, 2020. I’m going to go out on a limb here and speculate that there is a THIRD superseding, as the last events in the second one are from the Stratfor intrusion in 2011.
Because this seems like something the DOJ should DO something about …
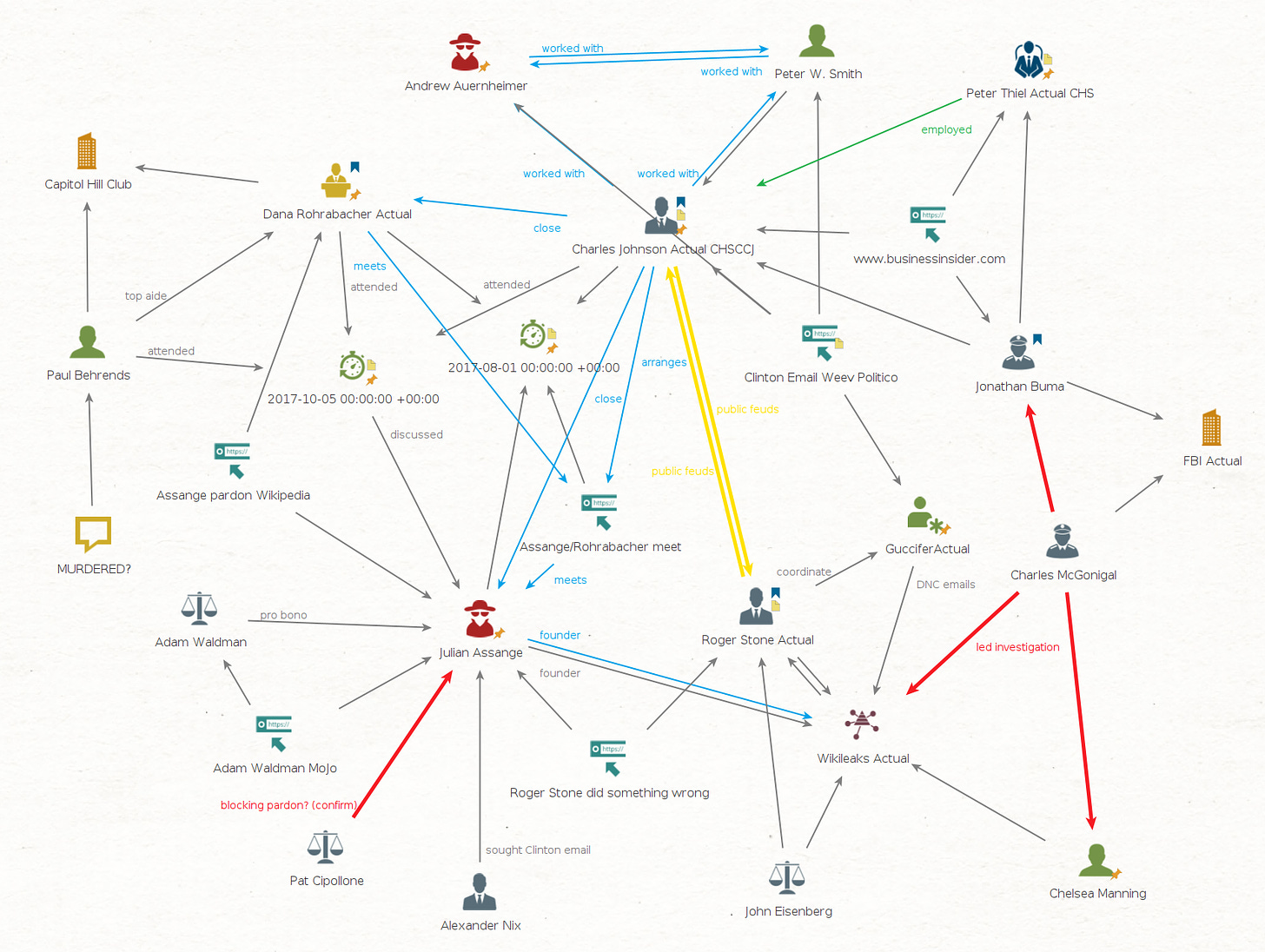
And then there’s the small matter of Charles Johnson and Peter Thiel being handled by FBI whistleblower Jonathan Buma …
These guys are all on my MAGA Metldown Maltego graph and it took me a LONG TIME to prune all the stuff around them in an effort to make this presentable. Johnson is a rare bird - a fellow trouble magnet, but with a couple orders of magnitude more trouble tentacles than me. I attended a couple of his Spaces on Twitter, but I didn’t care for some of the people that turned up, so I’ve settled for occasional summaries from someone else who is paying close attention.
Conclusion:
Despite Stone’s extraordinarily high profile in terms of the Russian interference in the U.S. election in 2016 and his role in the January 6th attack, there is literally no trace of the Power10 social botnet in any of the investigations.
Given that the person involved in developing the site may have also been involved in the mobile malware activities of Datablocks, this seems like something that SHOULD have received attention. This is couched in the language of possibility rather than fact; while OSINT took us a long way, there’s only so much that one can deduce from the public trails.
The curious segue taken by xive[.]io from U.S. political social media booster to a Bitcoin mining operation in Kazakhstan literally in the middle of its use is also really intriguing. Kazakhstan is a great place, right next door to Russia, not a lot of rules on what gets done there …
The curious story of the Power10 botnet was its own little subplot, having nothing to do with Assange. I would not have thought to connect the two stories in this fashion, that would have been the worst sort of conflation, but the last week or so, it’s become clear …
sOmEtHiNg’S uP
Having made this public, next I’m going to circulate the link in a couple private venues, make sure it gets seen by the right people. It would be nice to see some of that excess energy directed at, ya know, things that actually happened.