What Hunts You? is an article here about personal threat assessment, based on my experiences while wandering the dirty end of the playing field these last fifteen years. I pull this one out regularly, and in general this happens when people are faced with some new security problem, or tool, and they’re wrestling with how, or even IF they should use it.
I just noticed MITRE’s Workshop on Privacy Threat Modeling, and the Pattern and Action Nomenclature Of Privacy Threats In Context, which is a privacy threat taxonomy. Where we previously had to make do with my personal perspective, now we have the option of a formal model.
Attention Conservation Notice:
The vast majority of us meander through privacy threats without noticing and appreciating them. I think all of us could use improvement in this area and it’s nice to see a structured approach become available. If you are reading this Substack you already have some degree of concern in this area. So … I guess … you do you, but if you don’t, it’s inevitable someone else will.
PANOPTIC:
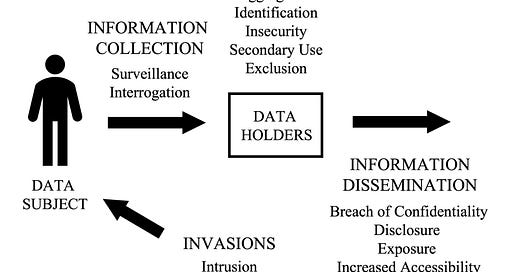
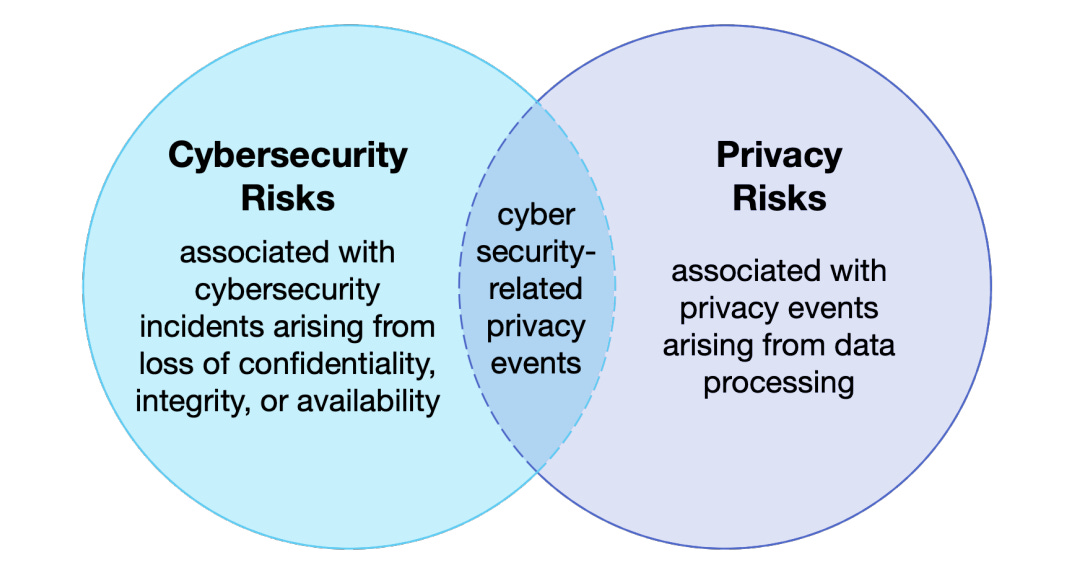
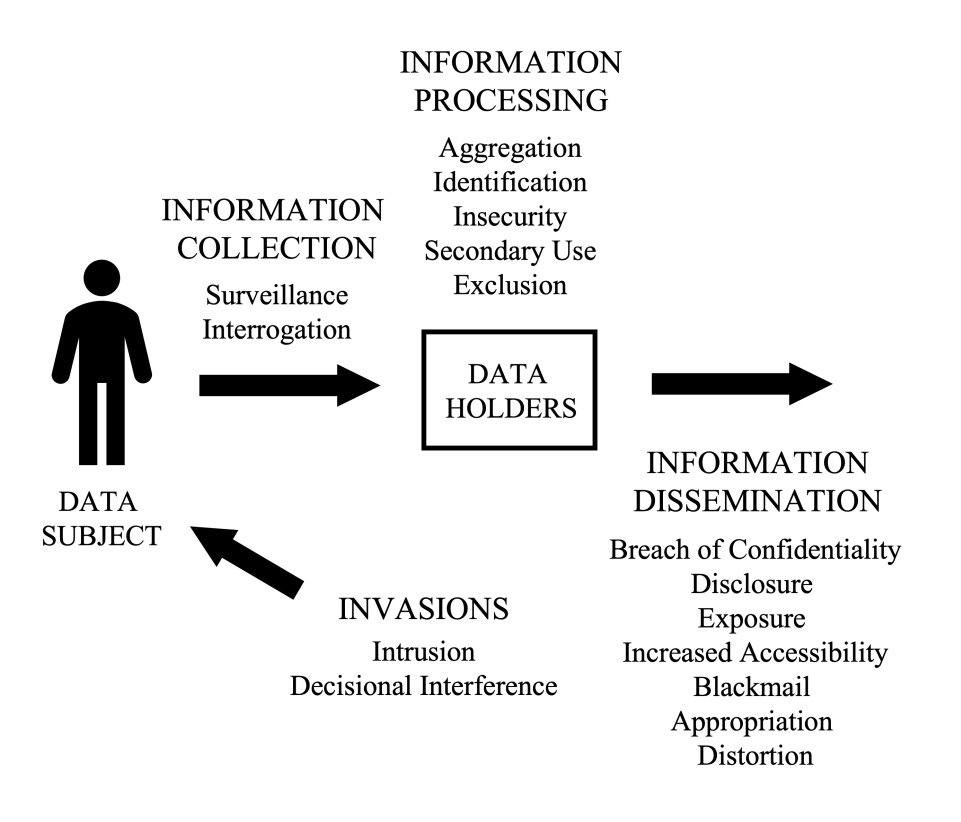
There is one thing that PANTOPIC is firmly, intentionally NOT, and that is “yet another take on cybersecurity issues”. The underlying model for the problem space is from Solove’s 2006 Taxonomy of Privacy. There’s a nice infographic for the concepts in the model.
So what’s the difference? One of the easily understood examples involves a company called Nomi, who were tracking people inside and outside retailers using Bluetooth sensors. Your phone’s Bluetooth has a MAC address, a unique device ID that is burned into the system, and if you’ve left your WiFi on that is also making a unique MAC address available over the air. This information gets tracked, perhaps hashed to anonymize it, but there are far too many ways to infer things from it. Nomi faced an FTC complaint over this practice.
If you’ve followed Tool Time here, you might have noticed how often burner phones come up in the Review. And recently there was an Actual Phone Security Consult. What do I say about these small, poorly secured computers in our pockets and purses?
Carrier numbers can give up your location.
Carrier numbers can be spirited away.
Carrier numbers get entangled with IRL services.
Carrier numbers get entangled with family & friends.
There are some technical intrusion hazards, but overall mobile devices even when working correctly are used in an invasive fashion.
Conclusion:
I opened the PANOPTIC material thinking it would be like The Online Operation Kill Chain, something that would be amenable to splitting into a month or a quarter worth of articles. Instead I find that there is the very first version of an assessment spreadsheet and talk of privacy red teaming. Unlike TOOKC, which was an enterprise level thing we tried to hammer into small unit doctrine, PANOPTIC is personal and it’s still forming.
This is a much better fit for those of you who contemplate getting involved in the endless online conflict scrum. But it’s not some facile ten point list from which we can pick and choose. The material forces me to stop, think, and then start checking the footnotes. It will be a rich vein to mine, obviously, but it’s going to be pick & shovel intellectual work, because we’ll be breaking new ground.
But on that note, I guess we now know what we’re doing for the rest of the first quarter of 2024.