Ten days ago when I declared we’re doing a Malign Influence Operations Safari for Q2 2024 I had no idea how far and how quickly things were going to escalate.
So without tipping off the targets just yet, let’s talk about getting to probable cause for FISA warrants. Briefly, U.S. law enforcement can not monitor U.S. nationals without jumping through the hoops to acquire a specific type of warrant, and looks like we’ve got the goods to trigger that.
Specifically, we’ve got some phone call records that reveal … curious patterns.
Attention Conservation Notice:
This is all about analytical tradecraft and I can’t show the actual goods. Assuming this process works you’ll learn who the lucky winners are via a story in a srs bsns national newspaper. There’s a lot of Hacks, Leaks, and Revelations type work in this and a good bit of Attribution of Advanced Persistent Threats. If you’ve never opened Maltego the lede is probably all you need.
Talking Around The Issue:
OK, so what we got are a log of calls that originate in an agency of a sanctioned nation and about a fifth of them, some five thousand calls, are to ten digit NANPA numbers. Thus far all of them have been U.S. area codes. There are two dozen origins that call six hundred numbers in North America. Half of the calls go to just the top 10% of recipients.
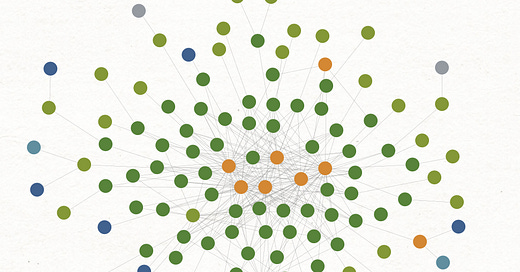
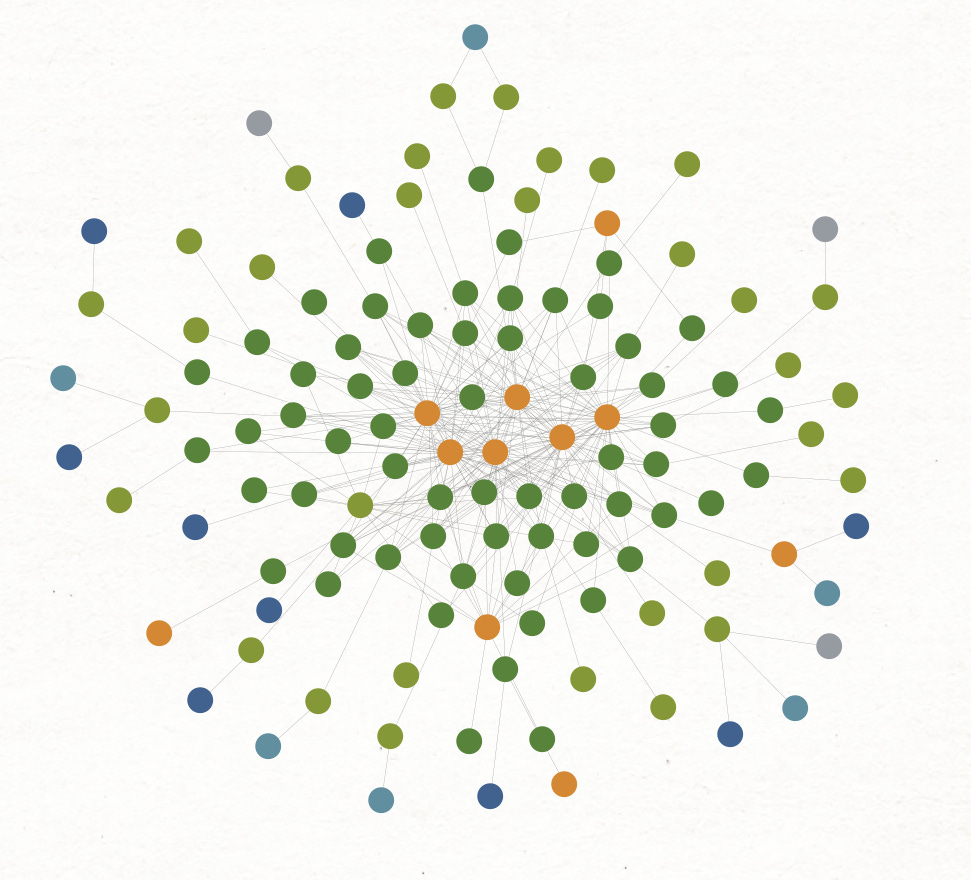
This first one is the frequent flyers graph and it could be better. The gold at the center are foreign origination points, the dark green around them are phone numbers, and the second ring of lighter green that many of you will not be able to differentiate are individual names. Some of the numbers are organizations, which show up as gold or dark blue dots. This is the 50% of calls going to a small group of ringleaders.
I also went at the bottom end of the set, to see what was lurking there. The lower left are calls originating from PSTN numbers in the foreign country, the rest are four digit internal extensions. The center left cluster are numbers associated with a penny ante cybercrime operation here in the U.S. that I believe is being run to conceal the activity of these NANPA numbered phones. Many of the others in both graphs are academics, journalists, and the like - people for whom contact with an agency of a foreign government might be work related and/or 1st Amendment protected activity. There are some overt foreign nationals who have North American numbers, a not unusual thing for people who travel internationally.
The juiciest bits are the obvious effort to conceal NANPA numbers under a cloud of a small dollar scams. Taken on their own, it’s the sort of thing that would not rise to the level of law enforcement attention. When seen with the foreign call origination, there’s obviously something here that needs further inspection. And there at the bottom right … a slip that’s put me on the trail of some internet infrastructure they have here in the west.
The APT Shuffle:
The call logs alone are sufficient for FISA attention, assuming they can be verified and there are a couple ways to do that. One involves my nose on the ground, the other involves someone, somewhere, who shall remain nameless, deciding this is a serious enough problem that they speak anonymously but on the record.
The thing that excites me here are the domains involved in the penny ante scam smoke screen and this tiny little infrastructure related leak at the lower right. I found this Sunday night, promoted the entities involved to a Maltego graph of their own, and then just walked away. If there is an opening there it’ll be in the historic data from RiskIQ, there’s nothing they could do to muddy the trail even if someone figures out what I’m talking about here and decides to notify the subjects.
The only vaguely magical thing in all this is that I have a knack for getting access to tools I could never afford, like RiskIQ and Semrush. The rest is just taking the experience I have running ISPs, voice carriers, and hosting, then applying that to the puzzle that’s been set before me.
Conclusion:
I’ve done a variety of things like this in the past. Who radicalized Cesar Sayoc? I know, so does the FBI, but it never made the news. The lack of attention on Roger Stone’s botnet was part of the reason this Substack is back in action. There’s a mishmash of other stuff like that, sometimes it gets mentioned, but more often than not once the job is done it’s just quietly filed.
Preserving American democracy in the 21st century involves citizen groups like the Sedition Hunters. Our government is simply too infiltrated by Christian Nationalists to tend to these problems without people like you and I shoring up the Fourth Estate and the FBI.
Some of you donated last month after I posted Artificial Intelligence For Disinfodrome. Thank you … and now you know why that got put on the back burner. Working this leak has inserted further delay, but it’s the good kind. There’s no commitment yet, but tending to this problem may open some doors we’d have never been able to access otherwise.
So cross your fingers, and if you’re able, I swear we’ll make effective, frugal use of any funds that turn up.