There is no honor among thieves. The lede from BreachForums v1 database leak is an OPSEC test for hackers is a real thigh slapper.
The entire database for the notorious BreachForums v1 hacking forum was released on Telegram Tuesday night, exposing a treasure trove of data, including members' information, private messages, cryptocurrency addresses, and every post on the forum.
This data comes from a database backup allegedly sold by Conor Fitzpatrick, aka Pompompurin. In 2022, after the RaidForums hacking forum was seized, Fitzpatrick launched BreachForums v1, which was later seized by the FBI after Fitzpatrick was arrested.
Fitzpatrick allegedly sold this database in July while he was out on bail. The data has since been circulating among different threat actors, with one attempting to sell it for $150,000 later that month.
While I do handle leaks, this particular disclosure doesn’t concern me, but it IS worth a look for a portion of the readership here.
Attention Conservation Notice: This will be a quick tour of the dirty end of the playing field. You should at least recognize when this stuff is happening, so you don’t get handed a bag to hold …
My Leak Doctrine:
There are four flavors of leaks that I touch. These are:
Data obtained from DDoSecrets - public interest material.
Data sourced by journalists.
Data obtained by whomever against international foes - Iran, Russia, etc.
FBI jurisdiction intrusion data on behalf of victims.
The journalism part is simply understood, Disinfodrome is a service used by journalists and researchers to explore large volumes of data that is of public interest. Among those datasets you find court documents, Congressional publications, FOIA material, and some intrusion data.
I will happily put my thumb in the eye of the IRGC, FSB/GRU/SVR, Belarus KGB, etc. The handful of countries that are the core of the threat against the global order established after World War II are fair game.
The last one is a bit unusual and it’s been a while since I’ve done such work. I had BlueLeaks content some years ago, an ankle biter snitch went to great lengths to get some evidence of this … and I had it because I’d been asked to evaluate the material for one of the affected agencies.
BreachForums:
Unlike DDoSecrets, which exists as a repository of public interest data, BreachForums was purely a criminal watering hole. The datasets available there were the proceeds of crimes and they were being sold to facilitate further criming. The origin story for the data being sold is usually some sort of technical intrusion and the bulk of the crimes being facilitated are identity theft related.
A local example that’s been dealing me fits is the Patelco ransomware attack. I’m not a customer of this particular credit union, but someone close to me is. They’ve had periods of no access to their funds and I’ve assisted them through the rough patches. I’m under employed and personally penniless, but there are a couple credit lines I can tap, and if repayment is fairly quick this is easily done. I see others who are affected, their problems are far more serious, and I have neither the means nor the motivation to assist them, but I do see how the harm has radiated.
Hardening yourself against this sort of thing is something I preach on the regular. An off the cuff summary of specific top level recommendations would be:
Lock every account you have with 2FA such as Authy, Duo, etc.
Conceal your carrier number with Google Voice.
Separate your communications and registration email addresses.
Compartmentalize your online purchasing from real banking.
Don’t creep around in the shadows with your daily driver laptop/phone.
Snitch Behavior:
As I covered in fairly exhaustive detail in Informantspotting, I had issues with attempted political prosecution before Andrew Breitbart dropped dead in the middle of a fight with me, and it escalated bigly after that. That post is pretty definitive, you’d better read it if you’re working with grassroots groups and they are at all near anything shady.
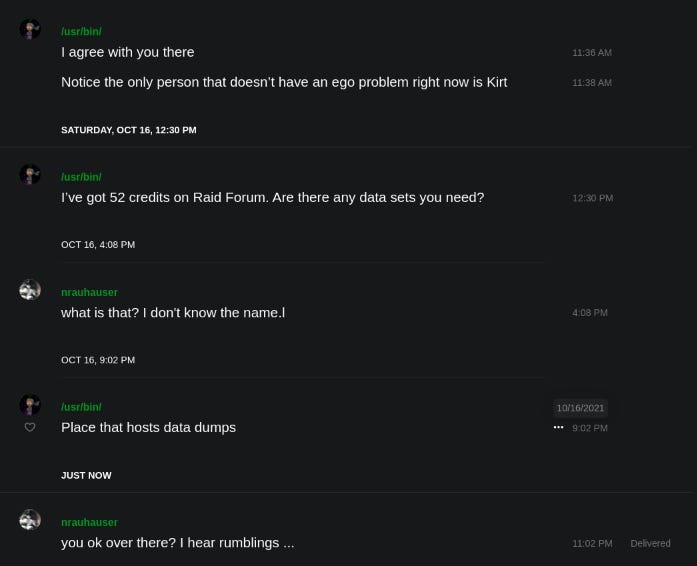
One episode I did not include in that article dates back to October of 2021. Recall that I spent the first three quarters of that year in proximity to Aubrey Cottle, the founder of 420chan. He was deeply involved in the burst of activity against right wing extremist websites that began with attention to Parler in late 2020. He has a stable long term handle, Kirtaner, and it’s typically shortened to Kirt in conversations.
So here’s a helpful fellow wanting to share some RaidForums credits with me. Because my focus is as described in the first section of this article, I have no reason to frequent such places. If I ever were to engage one of them I’d follow the usual protocol of paying cash for a burner, then using its hotspot function.
The operator of that account had never previously shown any knowledge of or signs of interest in intrusions. That he had such a thing and was offering it to me was a patently obvious attempt to identify my user information for RaidForums. There are situations where I’d accept something like that with the intent to see what the next move might be, but in that case the motivation was immediately obvious and conveying utter disinterest was the right thing to do.
Conclusion:
During the preparation for the PressTV article I was asked to describe myself for the sake of the Washington Post editor handling the story. They took all that I had to say and settled on “cybercrime and disinformation researcher”, and they’re the ones that added cybercrime to the mix. I would not have used that term myself, at least not then, but in looking back over what I do … yeah, I guess I do keep one foot partly in that world.
I’m a curious sort of daywalker, akin to Anton Gorodetsky, a “light other” who drinks blood so he can hunt vampires for the Night Watch. Part of the reason I get to do the things I do is my OIG complaint against the Dallas FBI field office. If someone with no history and no hardening tried to follow my lead, they’d get raided, deprived of any access to their systems, and forced to take a plea deal. First, I expect that and prepared for it, so it wouldn’t work. Second, elevating me to public notoriety has never been anything but a source of hard pain for those who thought that would harm me. Third and best of all, I’m pretty sure the USDOJ would rather eat an entire bucket of live toads sans condiments than provide me with any sort of opening to do discovery.
That being said …
There has been an icy wind blowing in the underworld for a while now. The PressTV article set off a cascade of stuff and “the scene” was even more jiggy than usual. I attributed it to “pre-election clean up”, which actually is a thing and it happens prior to every presidential election. Now we know a bit more about why they were acting like a troop of howler monkeys that just spotted a jaguar.
The above is a non-academic observation. While I have no exposure to BreachForums, I do have one of those journalist sourced leaks, and it’s getting attention from multiple journalists. Like the PressTV data, it’s multifaceted and the going is slow. Like the Epik intrusion, publication will trigger a howler monkeys v. jaguar reaction from Domestic Violent Extremists.
And as for you, constant reader, tread lightly, with Biden out and Harris in it’s getting sporty out there.