(Update: Kinda thought it might be a nothingburger right from the start, DailyDot did a review and confirmed this. They took a bunch of random stuff already known, pushed it into a pile, stuck an Anonymous sticker on it, and *presto* excitement. As the inventor of the nothingburger torrent, clear back in 2011, imitation is the highest form of flattery.)
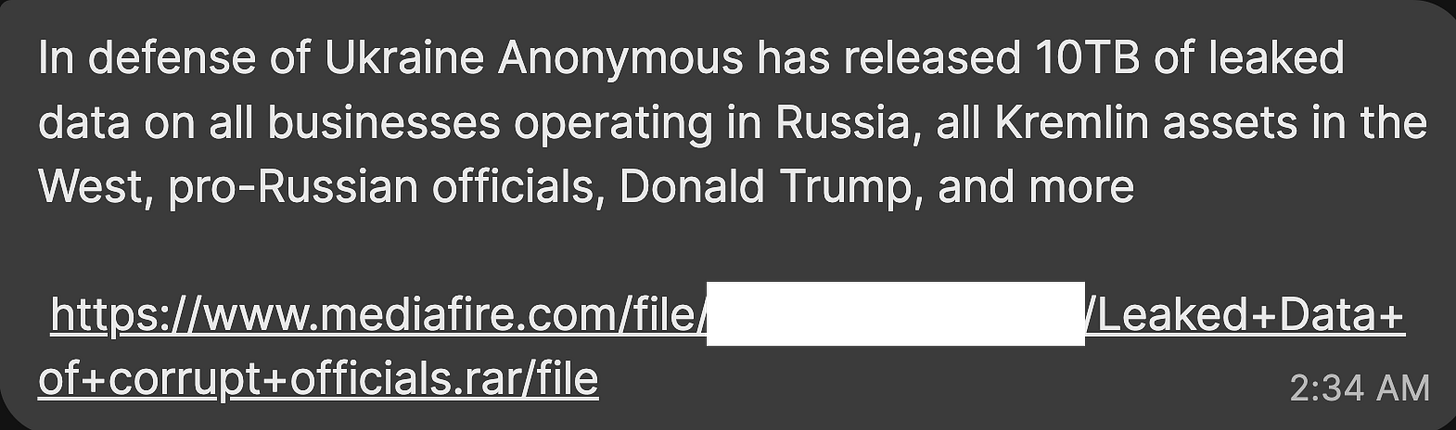
This turned up in a Signal chat this morning at 0234 Pacific time. The source for this is someone who always brings in good stuff, so I had a look at it.
I’m not providing the whole link (for reasons) but let’s walk through how to handle such a thing.
Attention Conservation Notice:
I’m not really awake, my favorite angry Latina has been chewing my ear since last night, and I am forced to again be a PHP ninja this morning. All bets are off re: accuracy and quality control.
Danger Zone:
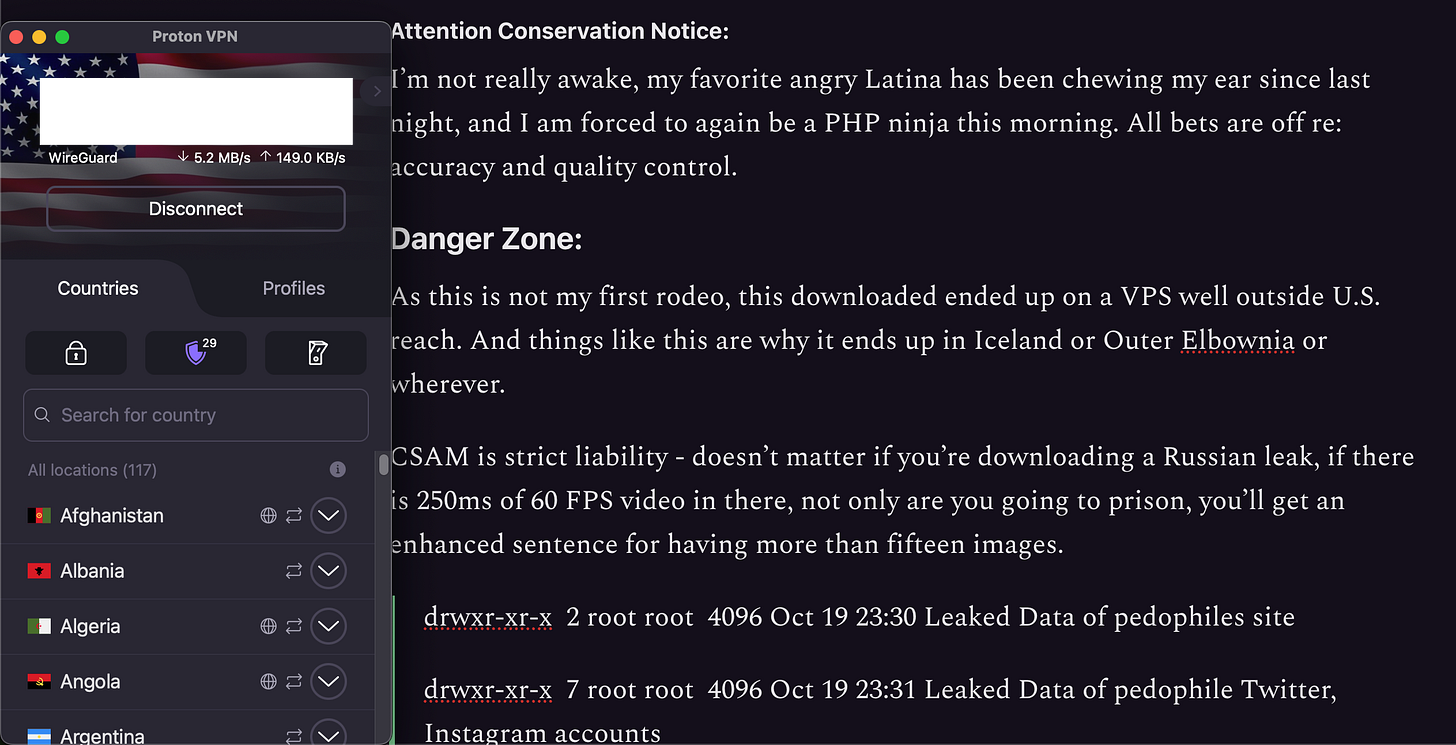
As this is not my first rodeo, this downloaded ended up on a VPS well outside U.S. reach. And things like this are why it ends up in Iceland or Outer Elbownia or wherever.
CSAM is strict liability - doesn’t matter if you’re downloading a Russian leak, doesn’t matter if you never looked at it, if there is 250ms of 60 FPS video in there, not only are you going to prison, you’ll get an enhanced sentence for having more than fifteen images.
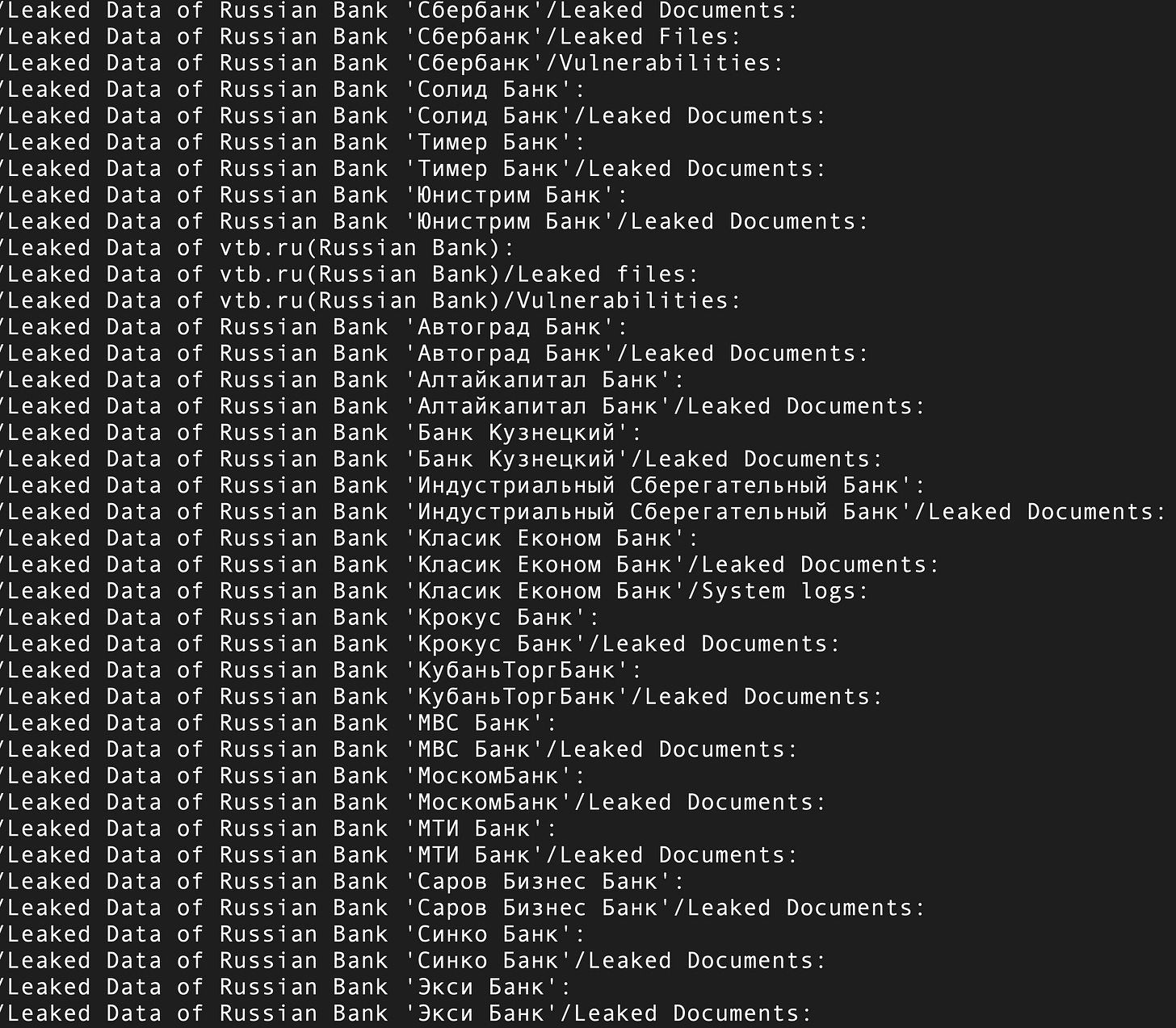
drwxr-xr-x 2 root root 4096 Oct 19 23:30 Leaked Data of pedophiles site
drwxr-xr-x 7 root root 4096 Oct 19 23:31 Leaked Data of pedophile Twitter, Instagram accounts
First Impression:
The use of mediafire[.]com is curious, can’t recall a leak originating there previously. How is an archive of this size still up four hours after being spotted? Curious … and the page reported the upload region is Ukraine. Now I’ve had Ukrainian VPSes that come and go, there are providers that take Monero and don’t ask stupid questions, but … *natural scene suspicion kicks in hard*
The MediaFire page for this wants you to sign up, log in, etc, etc. That is SO not Anonymous … below is how I know that. Why I don’t care is I still have a Chrome instance with ScriptSafe running, and ain’t nothing running on MediaFire, till I let ‘em in one by one. I find the whole thing suspicious. Just looking at it from a U.S. VPN exit, even Proton, makes me a trifle nervous.
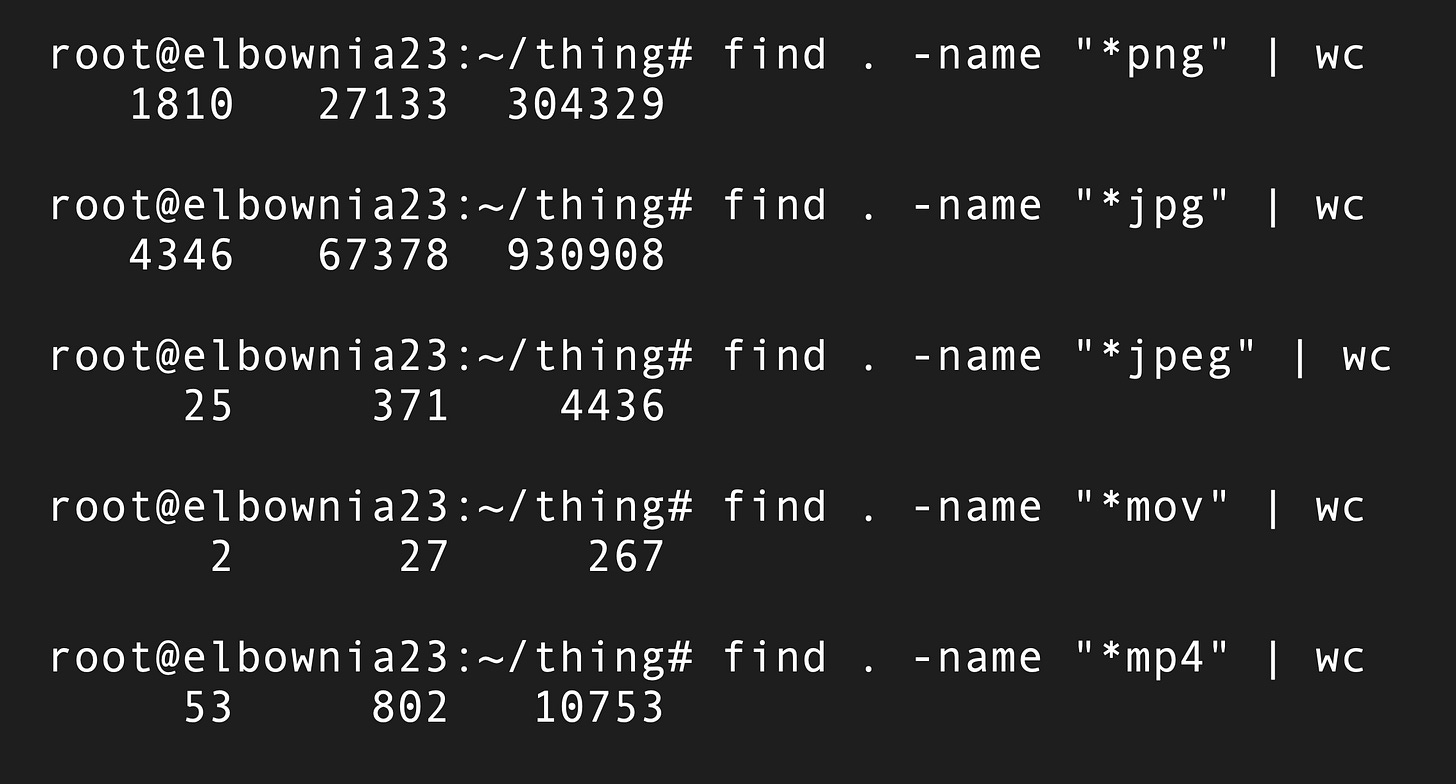
I can’t abide skids who leave spaces in folder names, especially at the top level. This is the data I’m examining.
openssl sha256 LeakedDataCorruptOfficials.rar
SHA256(LeakedDataCorruptOfficials.rar)= 3b8eb5a0c020ecd5f9bacdaf81ac35cfed200761835e9c537ccb7fc514b19edc
Further Paranoia:
Nope, not gonna examine this within the U.S. Life is too short, someone authorized, or someone highly skilled somewhere else can do this.
Let’s review:
There’s a suspicious leak
at a very suspicious time
with suspicious characteristics
There’s a VPS that was rented with Monero
in an uncooperative jurisdiction
and I’ve never logged into the provider without using a fail closed VPN config
The fail closed VPN config was a ProtonVPN secure core
and anything I have ended up there
Even More Paranoia:
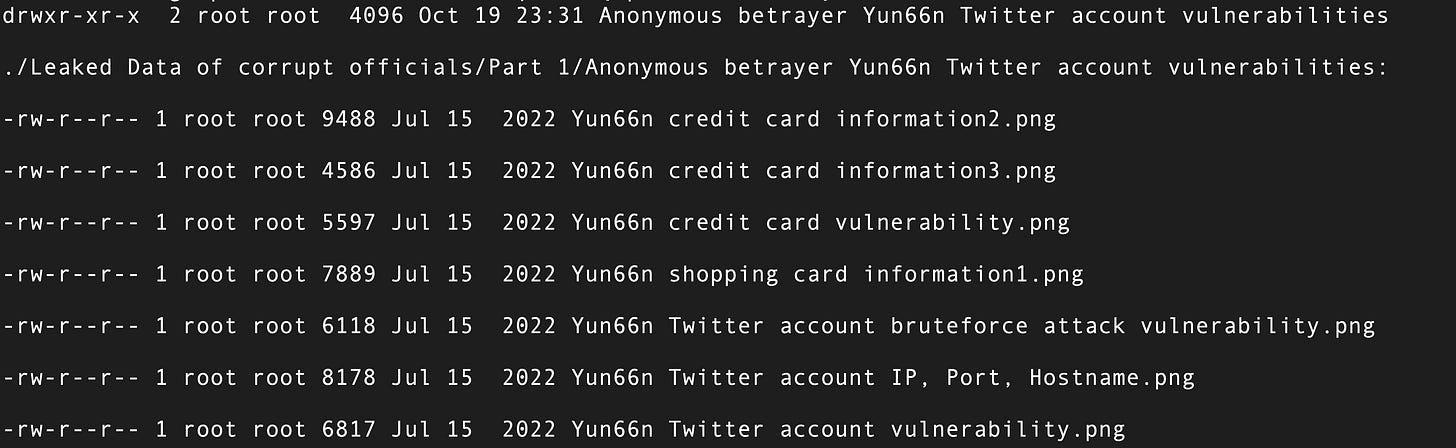
This leak is littered with stuff labeled “credit card”. Are you familiar with 18 U.S. Code § 1029 - Fraud and related activity in connection with access devices? I sure am, due to a dope fiend who got raided on live stream back in the day. Don’t end up like this guy …
Potentially Useful Stuff:
I wonder if the U.S. is going to accept Russian extradition requests. Given Trump’s frequent fellation of Putin, that’s not out of the realm of possibility.
Conclusion:
I spent an hour collecting and looking at it, then gave the link to a journalist who can handle such things w/o getting locked up. That VPS will be around for the next day or so, once the reporter gives me the thumbs up indicating they’ve got a copy, it’ll get recycled.
My take after this quick “battlefield triage” is that this is a single source player, perhaps using a Windows system, who collects whatever they see, and they may be trying to work some of it in some fashion. Maybe they’re trying stuff against sites in a Kali VM, maybe they’re in a bunch of channels and their role is passing this stuff around to anyone who seems like they might try to use it.
Please read Pitiful Brandfagging for my recent assessment on anon:
Anonymous is, has been, and will remain DEAD.
Another reporter popped up just as I was finishing this. I’d say this one is well in hand ...